Basics of Java Serialization and Deserialization
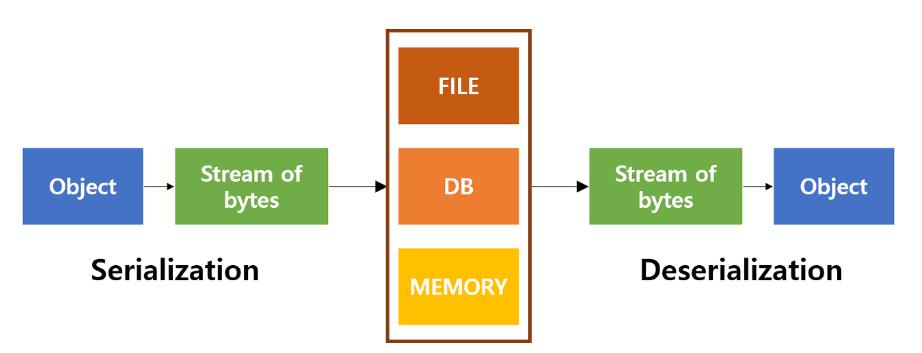
Java serialization is a process where an object’s state is converted into a byte stream, enabling its storage in a file or transmission over a network. To achieve serialization in Java, a class must either adopt the java.io.Serializable interface or the java.io.Externalizable interface. The Serializable interface serves as a marker, signaling the Java runtime that the class is eligible for this process. It doesn’t require any method implementations. In contrast, Externalizable is more complex, providing full control over the serialization algorithm by enforcing the implementation of writeExternal and readExternal methods.
During the serialization process, object states are converted into byte sequences. This encoding includes metadata about the object’s type and the types of fields stored within, though it doesn’t include any instance-specific methods.
Example-
import java.io.*;
// A simple class representing a Person
class Person implements Serializable {
private String name;
private int age;
public Person(String name, int age) {
this.name = name;
this.age = age;
}
public String getName() {
return name;
}
public int getAge() {
return age;
}
}
public class SerializationExample {
public static void main(String[] args) {
// Create a Person object
Person person = new Person("John", 30);
try {
// Serialize the object
FileOutputStream fileOut = new FileOutputStream("person.ser");
ObjectOutputStream out = new ObjectOutputStream(fileOut);
out.writeObject(person);
out.close();
fileOut.close();
System.out.println("Object serialized successfully.");
} catch (IOException e) {
e.printStackTrace();
}
}
}
In this example, the Person class implements the Serializable interface, indicating that its instances can be serialized. The SerializationExample class creates a Person object and serializes it to a file named “person.ser” using ObjectOutputStream.
Deserialization:
Deserialization is the process of reconstructing an object from byte streams. Java reconstructs an object from these sequences, using the class description incorporated in the encoded data. This operation doesn’t use conventional constructors; instead, it recreates an object using information directly from the input byte stream.
public class DeserializationExample {
public static void main(String[] args) {
try {
// Deserialize the object
FileInputStream fileIn = new FileInputStream("person.ser");
ObjectInputStream in = new ObjectInputStream(fileIn);
Person deserializedPerson = (Person) in.readObject();
in.close();
fileIn.close();
// Display deserialized object's details
System.out.println("Deserialized Object:");
System.out.println("Name: " + deserializedPerson.getName());
System.out.println("Age: " + deserializedPerson.getAge());
} catch (IOException | ClassNotFoundException e) {
e.printStackTrace();
}
}
}
In this extended example, the DeserializationExample class reads the serialized Person object from the file “person.ser” and reconstructs it using ObjectInputStream. The deserialized Person object’s details are then displayed.
Safeguarding Objects: The Importance of Cautious Serialization in Java
Developers must use serialization cautiously, given its capabilities of rebuilding objects and potentially executing unintended operations if untrustworthy data gets deserialized. Safeguarding objects during deserialization requires careful consideration. Using features like serialization filters introduced in newer versions of Java can act as gatekeepers that decide which classes are deemed safe for deserialization.
As programmers fortify their systems with robustness against potential attackers by exercising good judgment about trust boundaries, actively updating dependencies, and reviewing MIME types, they embody the spirit of diligent coders making informed choices about incorporating serialized data communications in their Java applications.
Security Risks in Deserialization
Handling deserialized data poses inherent security risks, notably when external sources are involved. Malicious actors may seize opportunities within this processing phase to manipulate or alter the object state, exploiting vulnerabilities for remote code execution or other nefarious purposes.
One key vulnerability surfaces when serialized objects, infused with malicious intent, enter a system unscrutinized. Attackers carefully prepare crafted byte streams that, once deserialized, can trigger unintended effects on application behavior or lead to arbitrary code execution.
Such risks are amplified by the common practice of processing serialized data from widely accessible endpoints that interact with various user-generated content or unsecured external systems. Oversights in these interactive zones can leave a system vulnerable to receiving and processing unsafe serialized objects.
Another significant concern is the manipulation of serialization metadata. Attackers can tamper with class descriptors or reroute them to different classes that embody malicious activities upon initialization. Relying on the integrity of the type and nature of deserialized objects solely based on received data becomes a vulnerability.
The use of signed objects or implementing thorough validation checks can act as a defensive layer against corrupted serialized data. Another potential countermeasure involves leveraging serialization proxy patterns which are less susceptible to tampering, or employing whitelist filtering that restricts which classes can be deserialized based on pre-defined safe lists. Even these measures have their limits and must be continually tested and updated in response to emerging threats.
Preventative Measures Against Deserialization Attacks
Given the severity and subtlety of deserialization threats, developers must systematically implement defensive measures. Using serialization filters is an ideal mechanism for mitigating such vulnerabilities. A serialization filter acts as a protocol by specifying which classes can or cannot be deserialized. This technique establishes a validation layer at the entry point of the deserialization process, ensuring that only objects from trusted and safe classes are processed.
Implementing input validation introduces another robust layer of defense. It involves scrutinizing incoming data for integrity and legitimacy before it undergoes deserialization. Developers should rigorously validate all data against a set of strict rules or schemas which dictate expected formats, types, and values of fields within the serialized objects.
Adhering to the principle of least privilege is essential in further reducing the risks associated with deserialization. Running processes with minimal permissions necessary reduces the attack surface. If an attack does occur, its potential to inflict damage or compromise vital system functionalities is considerably hindered.
Taking proactive measures for regular updates and patches for all components also diminishes the chance of deserialization vulnerabilities. Vendors often release updates as soon as mitigation strategies are available. Staying current with these updates can safeguard systems against known vulnerabilities that could be exploited via serialized objects.
For applications where high security is crucial and serialization is unavoidable, utilizing architecture patterns, like employing serialization gateways that centrally handle all serialization and deserialization activities, can offer control and audit capabilities. This gateway ensures all serialized data conforms to strict security policies before being passed into the larger system.
Creating a security-focused development culture remains paramount. Continually educating and training developers on secure coding practices, with an emphasis on serialization flaws and their impacts, fosters an environment where security is a prime concern throughout the application lifecycle.
Real-World Exploitation of Deserialization
As we explore the mechanics of exploitation through Java deserialization, understanding real-world cases enhances our comprehension of these vulnerabilities. One prominent tool that exemplifies these exploitation arsenals is ysoserial. Originally designed as a proof-of-concept, ysoserial is a repository that houses a suite of utilities demonstrating the insecurity of several popular Java libraries through gadget chains. These chains string together sequences of classes or methods which, when manipulated in conjunction with deserialization vulnerabilities, allow for execution of malicious code on the affected systems.
Gadget chains work because many innocuous-seeming classes within common Java libraries hold methods that execute substantial operations. When deserialized improperly, these arbitrary method invocations launch more than just benign operations—they can enact commands, modify server-side mechanisms, or disrupt processes centrally orchestrated through Java applications.
In dissecting notable exploits, let’s consider an example from the oft-quoted Apache Commons Collections, a suite of classes from a popular Java library used in diverse systems. Attack vectors in this library were made prominent around 2015 when researchers discovered deserialization flaws that could leverage the library’s complex data-transforming methods to execute algebraic operations or runtime commands.1 These interactions typically commenced with manipulated inputs to certain API endpoints designed to deserialize incoming data.
In a practical scenario, imagine a business application that takes serialized user profiles from clients and deserializes them server-side for processing. An attacker could tweak serialized content targeted at this endpoint using a crafted sequence borrowed from Apache Commons Collections, injected through ysoserial to remotely open network connections, bypass authentication, or divert transaction data paths.
Preventing the damage doesn’t rest solely on curtailing gadget chains but extends into architectural territory where developers safeguard sensitive endpoints against malicious machinations. Limiting the classes that can be deserialized—through explicit white-listing—substantially blocks unplanned execution pathways. Systematically evaluating third-party libraries for vulnerabilities before integration also forms a crucial defensive line.
Tools and Techniques for Identifying Vulnerabilities
Developed by the research team at Bishop Fox, GadgetProbe is an innovative tool arming developers and security researchers with deeper insights into deserialization vulnerabilities. GadgetProbe streamlines the extensive trial-and-error process of identifying exploitable Java classes. Fundamentally, it leverages DNS to query a target application, awaiting responses that confirm whether certain Java classes and versions reside within the target’s classpath.2 Armed with this information, security specialists can map out potential intrusion paths or detect probable breaches more efficiently.
Shifting focus towards successful vulnerability identification, blackbox and whitebox testing contexts establish distinct landscapes for conducting assessments.
- Blackbox testing: In a blackbox environment, where the internal code dynamics remain hidden, tools like GadgetProbe or ysoserial play pivotal roles. Without knowing the internal workings, the tester probes with diverse serialized payloads and observes for effects, such as unexpected behaviors or crashes.
- Whitebox testing: Given direct access to the codebase in whitebox testing, a more granular investigation is enabled. Reviewing the source code carefully for classes implementing
SerializableorExternalizablewithout appropriate caution opens floodgates to targeted explorations. Tools like static analysis software or focused aids like IDE plugins help identify hazardous deserialization patterns swiftly. Maneuvers such as examining customreadObjectmethods that directly manage incoming data provide essential indicators of vulnerability.
For preventive developers, the combination of dynamic payload injection and strict code review fosters a shield against anticipated attacks. In practice, weaving a series of synthetic attack scenarios tailored from detected susceptibilities nourishes a competitive warp of deploying potentially weak segments under simulated breach scenarios. This proactive scrimmage, reciprocally educational for developers and testers, enriches a mutual understanding of battlefield strategies in safeguarding Java landscapes.
In conclusion, while Java serialization simplifies data storage and transfer, it also necessitates vigilant security measures to protect applications from deserialization attacks. Developers must integrate stringent safeguards and continuously update their defensive strategies to maintain the integrity and security of their systems.
Experience the future of content creation with Writio. This article was crafted by Writio.
- Breen J. What Do WebLogic, WebSphere, JBoss, Jenkins, OpenNMS, and Your Application Have in Common? This Vulnerability. FoxGlove Security. Published January 28, 2015.
- Spring T. Detecting Deserialization Bugs with DNS Exfiltration using GadgetProbe. Bishop Fox. Published September 29, 2022.