|
Getting your Trinity Audio player ready... |
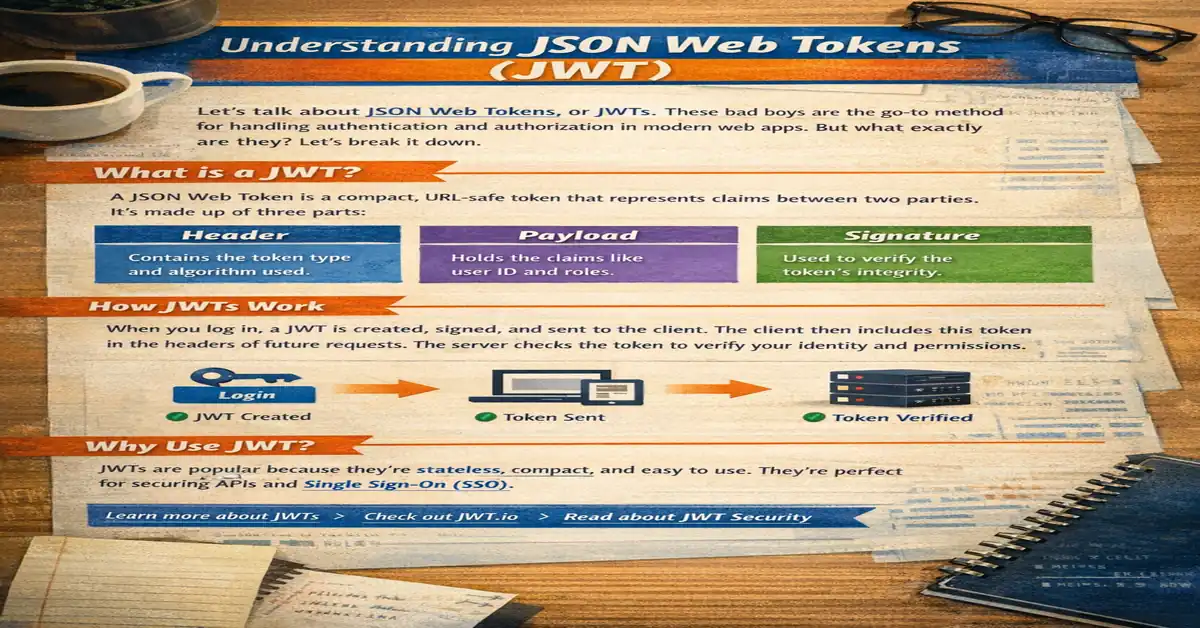
JWT, or JSON Web Token, is a compact, URL-safe way to represent claims between two parties. It is widely used for authentication, authorization, and secure data transmission. JWT allows servers to verify requests without storing session data, making it a popular choice in modern web applications.
How JWT Works
A JWT consists of three parts: Header, Payload, and Signature.
- Header: Typically contains the token type (JWT) and the signing algorithm (e.g., HMAC SHA256).
- Payload: Contains claims, which are statements about an entity (usually the user) and additional metadata.
- Signature: Ensures the token hasn’t been altered. It is created by combining the encoded header, payload, a secret key, and the signing algorithm.
Tokens are encoded in Base64Url and concatenated with periods: header.payload.signature.
Example Structure
eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9
.
eyJzdWIiOiIxMjM0NTY3ODkwIiwibmFtZSI6IkFyc2FsYW4iLCJpYXQiOjE1MTYyMzkwMjJ9
.
SflKxwRJSMeKKF2QT4fwpMeJf36POk6yJV_adQssw5c
Use Cases of JWT
- Authentication: Users receive a token upon login. The server validates it for subsequent requests.
- Authorization: JWT can carry user roles and permissions, allowing access control.
- Information Exchange: JWTs are signed, ensuring the data integrity between parties.
Advantages
- Stateless authentication reduces server memory load.
- Cross-platform and language-independent.
- Compact and URL-safe.
Security Considerations
- Always use HTTPS to prevent token interception.
- Keep the secret key secure.
- Avoid storing sensitive information in the payload.
- Set token expiration (
exp) to limit validity.
Popular Libraries
- jsonwebtoken (Node.js)
- JWT.io for debugging and testing tokens.
- PyJWT (Python)
Conclusion
JWT is a versatile tool for secure communication in modern web applications. By understanding its structure and best practices, developers can implement efficient, scalable authentication and authorization systems.
Arsalan Malik is a passionate Software Engineer and the Founder of Makemychance.com. A proud CDAC-qualified developer, Arsalan specializes in full-stack web development, with expertise in technologies like Node.js, PHP, WordPress, React, and modern CSS frameworks.
He actively shares his knowledge and insights with the developer community on platforms like Dev.to and engages with professionals worldwide through LinkedIn.
Arsalan believes in building real-world projects that not only solve problems but also educate and empower users. His mission is to make technology simple, accessible, and impactful for everyone.
Join us on dev community